【干货】华为企业网络典型配置案例
发布作者:微思网络 发布时间:2017-09-11 浏览量:0次
介绍:
下面为一般企业网络的结构、规划以及配置。
对内网部门划分vlan、无线配置、服务器的映射以及内网之间的互访都做了介绍。
1.各部门、服务器、无线都独立一个网段。
2.无线网络采用旁挂直接转发模式。
3.无线网络不能访问公司内网资源、只允许上网。
设备:
外网防火墙:USG5120
核心: S5700
接入: S3700
无线控制器:AC6005
无线AP:AP6010DN-AGN
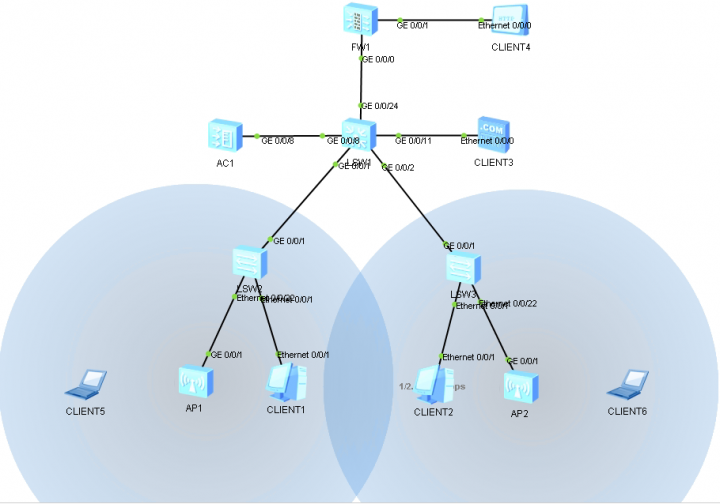
网络拓扑:
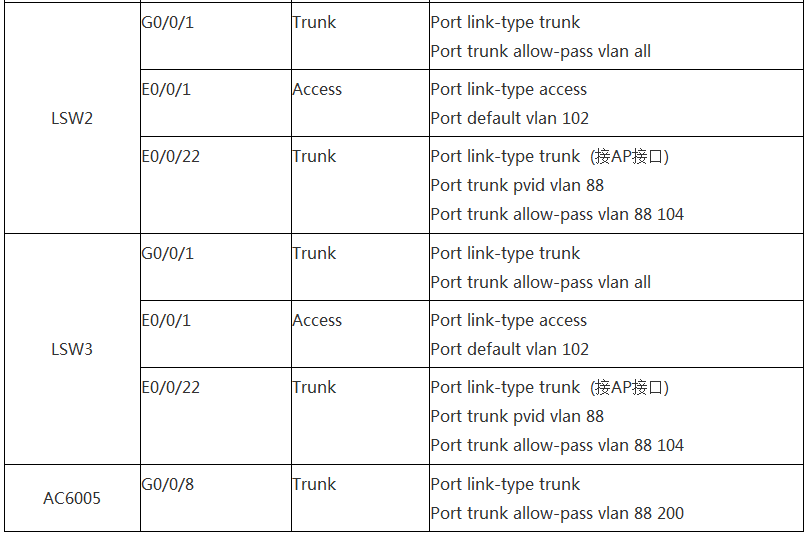
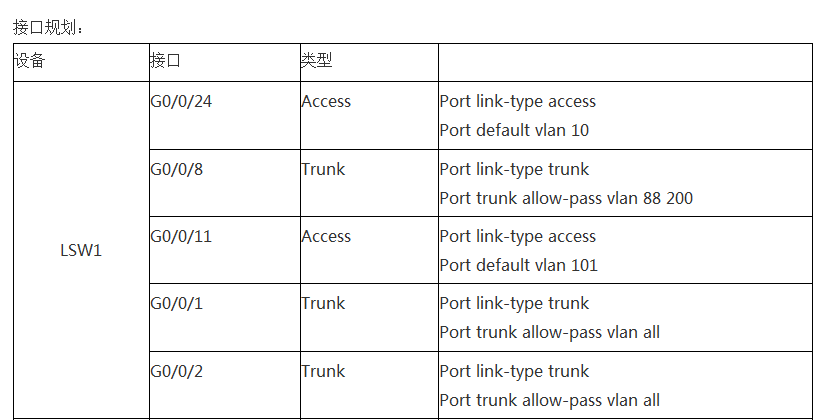
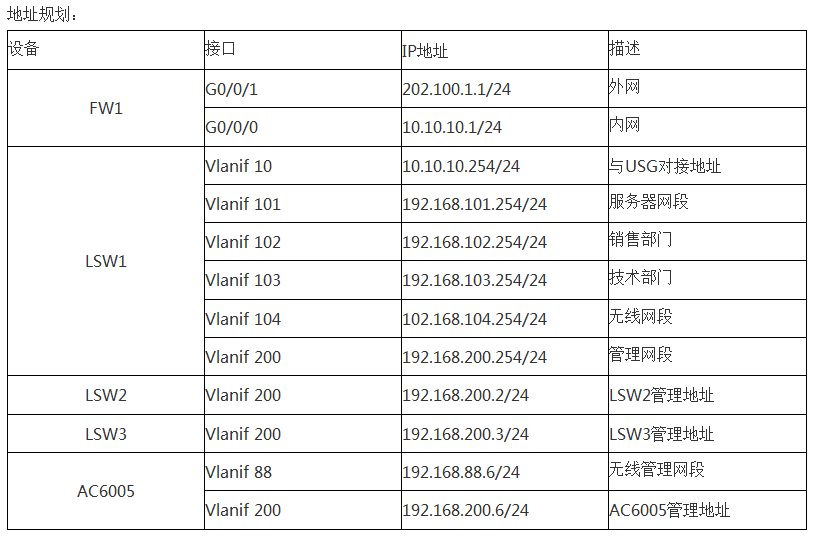
地址规划:

操作步骤:
1. 防火墙配置。
#
sysname FW1
#
interface GigabitEthernet0/0/0
alias Lan
ip address 10.10.10.1 255.255.255.0
#
interface GigabitEthernet0/0/1
alias Wan
ip address 202.100.1.1 255.255.255.0
#
#
firewall zone trust
add interface GigabitEthernet0/0/0
#
firewall zone untrust
add interface GigabitEthernet0/0/1
#
ip route-static 0.0.0.0 0.0.0.0 202.100.1.2
ip route-static 192.168.0.0 255.255.0.0 10.10.10.254
#
nat-policy interzone trust untrust outbound
policy 1
action source-nat
easy-ip GigabitEthernet0/0/1
#
firewall packet-filter default permit interzone trust untrust direction outbound //允许内网到外网的默认域间规则
#
2. LSW配置。
#
sysname LSW1
#
vlan batch 10 88 101 to 104 200
#
dhcp enable
#
interface Vlanif10
ip address 10.10.10.254 255.255.255.0
#
interface Vlanif101
description Server
ip address 192.168.101.254 255.255.255.0
#
interface Vlanif102
ip address 192.168.102.254 255.255.255.0
#
interface Vlanif103
ip address 192.168.103.254 255.255.255.0
#
interface Vlanif104
description WLAN-STA
ip address 192.168.104.254 255.255.255.0
dhcp select interface
dhcp server dns-list 192.168.101.2
#
interface Vlanif200
description Manager
ip address 192.168.200.254 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan all
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan all
#
interface GigabitEthernet0/0/8
port link-type trunk
port trunk allow-pass vlan 88 200
#
interface GigabitEthernet0/0/11
port link-type access
port default vlan 101
#
interface GigabitEthernet0/0/24
port link-type access
port default vlan 10
#
ip route-static 0.0.0.0 0.0.0.0 10.10.10.1
#
3. LSW2配置。
#
sysname LSW2
#
vlan batch 88 102 to 104 200
#
interface Vlanif200
ip address 192.168.200.2 255.255.255.0
#
interface Ethernet0/0/1
port link-type access
port default vlan 102
#
interface Ethernet0/0/22
port link-type trunk
port trunk pvid vlan 88
port trunk allow-pass vlan 88 104
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan all
#
ip route-static 0.0.0.0 0.0.0.0 192.168.200.254
#
4. LSW3配置。
#
sysname LSW3
#
vlan batch 88 102 to 104 200
#
interface Vlanif200
ip address 192.168.200.3 255.255.255.0
#
interface Ethernet0/0/1
port link-type access
port default vlan 103
#
interface Ethernet0/0/22
port link-type trunk
port trunk pvid vlan 88
port trunk allow-pass vlan 88 104
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan all
#
ip route-static 0.0.0.0 0.0.0.0 192.168.200.254
#
5. AC6005配置。
Vlan 88为无线AP管理网段、配置DHCP为AP分配地址。
#
sysname AC6005
#
vlan batch 88 200
#
dhcp enable
#
interface Vlanif88
ip address 192.168.88.6 255.255.255.0
dhcp select interface
#
interface Vlanif200
ip address 192.168.200.6 255.255.255.0
#
interface GigabitEthernet0/0/8
port link-type trunk
port trunk allow-pass vlan 88 200
#
interface Wlan-Ess104
port hybrid untagged vlan 104
#
wlan
wlan ac source interface vlanif88
ap-auth-mode no-auth
wmm-profile name wmm1 id 1
traffic-profile name tra1 id 1
security-profile name sec1 id 1
service-set name ser1 id 1
wlan-ess 104
ssid HUAWEI
traffic-profile id 1
security-profile id 1
service-vlan 104
radio-profile name radio1 id 1
wmm-profile id 1
#
等待AP上线后、AP绑定射频与服务集。
#
ap 0 radio 0
radio-profile id 1
service-set id 1 wlan 1
ap 1 radio 0
radio-profile id 1
service-set id 1 wlan 1
#
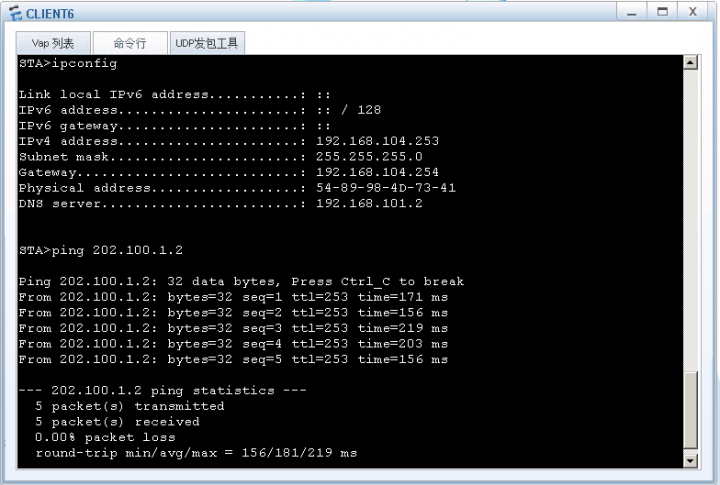
无线网络测试。
6. 内网服务器映射到外网、供外部用户访问。
#
nat server protocol tcp global 202.100.1.1 www inside 192.168.101.2 www
#
并要在防火墙配置转发策略、允许访问服务器。防火墙默认为拒绝访问。
#
policy interzone trust untrust inbound
policy 1
action permit
policy service service-set http
policy destination 192.168.101.2 0
#
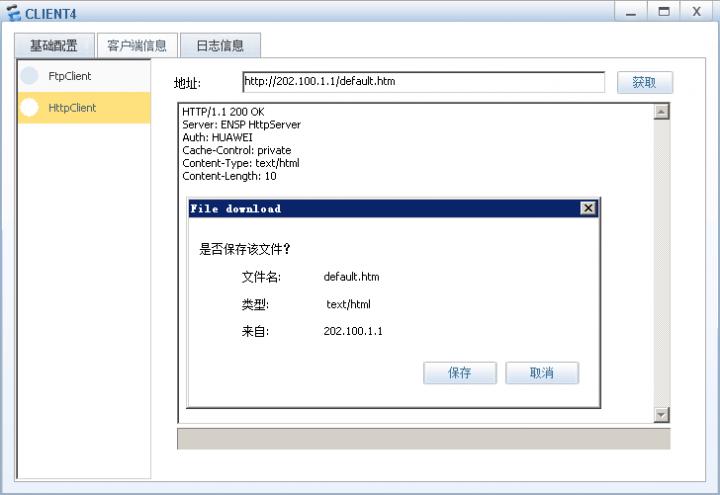
测试从外网访问内部服务器。
服务器设置:
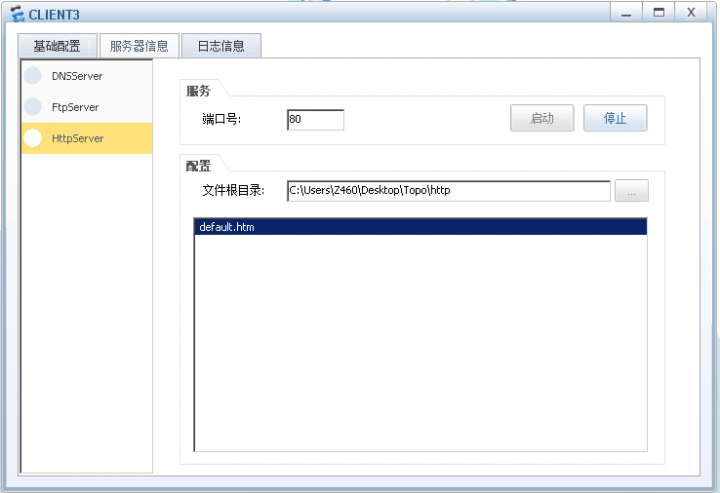
客户端访问测试:
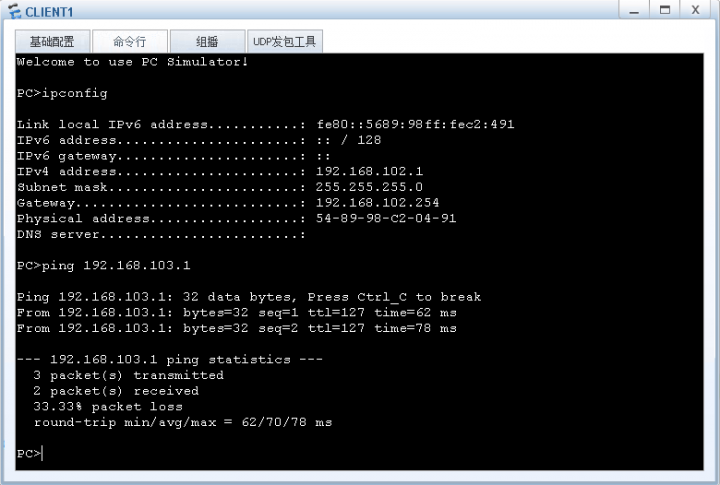
7. 部门之间互访测试。
CLIENT1 PING CLIENT2
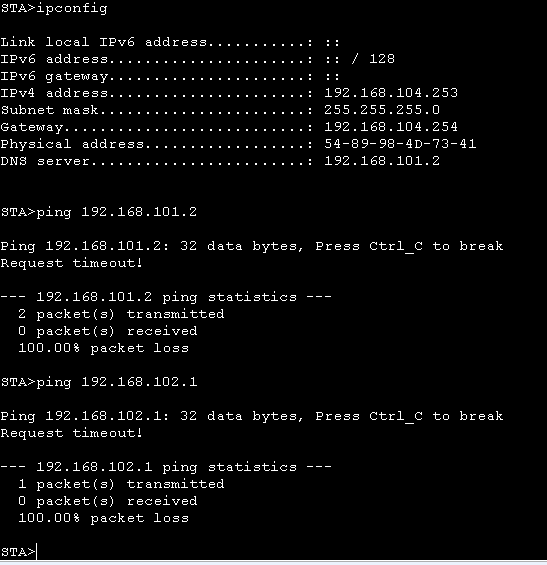
8. 访问之间做限制、无线接入用户无法访问销售部门、技术部门和服务器。
访问限制配置在核心交换机上:
#
acl number 3000
rule 5 permit ip source 192.168.104.0 0.0.0.255 destination 192.168.101.0 0.0.0.255
rule 10 permit ip source 192.168.104.0 0.0.0.255 destination 192.168.102.0 0.0.0.255
rule 15 permit ip source 192.168.104.0 0.0.0.255 destination 192.168.103.0 0.0.0.255
#
traffic classifier c1
if-match acl 3000
#
traffic behavior b1
deny
#
traffic policy p1
classifier c1 behavior b1
#
drop-profile default
#
vlan 104
traffic-policy p1 inbound
#
配置后测试:
☂☂☂☂☂☂☂☂
有些命令已更改,下面贴一下现在的命令:
现在在用的AC6005配置
#
来源:厦门ccna培训哪家好之华为企业互动社区
链接:http://support.huawei.com/huaweiconnect/enterprise/forum.php?mod=viewthread&tid=295783&extra=page%3D&page=1
http secure-server ssl-policy default_policy
http server enable
#
vlan batch 88 90 99
#
authentication-profile name dot1x_authen_profile
authentication-profile name mac_authen_profile
authentication-profile name portal_authen_profile
authentication-profile name macportal_authen_profile
#
dot1x-access-profile name dot1x_access_profile
mac-access-profile name mac_access_profile
#
dhcp enable
#
diffserv domain default
#
radius-server template default
#
pki realm default
enrollment self-signed
#
ssl policy default_policy type server
pki-realm default
#
acl number 2001
rule 10 permit source 192.168.0.199 0
rule 15 permit source 192.168.0.6 0
#
free-rule-template name default_free_rule
#
portal-access-profile name portal_access_profile
#
ip pool 1
#
aaa
authentication-scheme default
authentication-scheme radius
authentication-mode radius
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password irreversible-cipher %^%#6)l-&>+[)GN^jMDkBIsT}^nA4Kp^B3a4z|&lbvb-9vv'$uRxD~@k4'.E*O+L%^%#
local-user admin privilege level 15
local-user admin service-type telnet http
local-user telnet password irreversible-cipher %^%#c.izI-/~[HN4utOqT_X:F=_s0!<mj*=8amdc)si1hd2xh9m!' local-user telnet privilege level 15
#
interface Vlanif1
ip address 169.254.1.1 255.255.0.0
#
interface Vlanif88
ip address 10.1.88.1 255.255.255.0
dhcp select interface
#
interface Vlanif99
ip address 192.168.1.224 255.255.254.0
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
interface GigabitEthernet0/0/2
#
interface GigabitEthernet0/0/3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
interface NULL0
#
info-center timestamp log format-date
#
undo snmp-agent
#
ssh client first-time enable
stelnet server enable
undo telnet ipv6 server enable
ssh server secure-algorithms cipher aes256_ctr aes128_ctr aes256_cbc aes128 3des
ssh server secure-algorithms hmac sha2_256 sha2_256_96 sha1 sha1_96 md5 md5_96
ssh client secure-algorithms cipher aes256_ctr aes128_ctr aes256_cbc aes128 3des
ssh client secure-algorithms hmac sha2_256 sha2_256_96 sha1 sha1_96 md5 md5_96
#
capwap source interface vlanif88
#
user-interface maximum-vty 8
user-interface con 0
authentication-mode password
set authentication password cipher %^%#,s$,*,)&YGuva(Y
user-interface vty 0 4
acl 2001 inbound
authentication-mode aaa
protocol inbound all
user-interface vty 5 7
acl 2001 inbound
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
protocol inbound all
#
wlan
traffic-profile name default
traffic-profile name p1
rate-limit client up 10000
rate-limit client down 10000
security-profile name default
security-profile name default-wds
security wpa2 psk pass-phrase %^%#ro!\MZ&k0HRECV*riy463<sxn$c8}e=l\tek9z&e%^%# security-profile name default-mesh
security wpa2 psk pass-phrase %^%#hu]^OSnh2FiGXx.ps+]5'^foJ-kjG!Gua<ednioj%^%# security-profile name tftc
security wpa-wpa2 psk pass-phrase %^%#GjOs7\AA(QnC($)c1R]5sx!`C)\|f(ci'$0%^%# aes
security-profile name T-yf5
security wpa-wpa2 dot1x aes
security-profile name Tguest
security wpa-wpa2 psk pass-phrase %^%#+:@Z/_w;dJC`8v7cS@`!<g=;7lkied!w)r2p^h`9%^%# ssid-profile name tftc
ssid T-YF
max-sta-number 20
ssid-profile name T-yf5
ssid T-yf5
max-sta-number 23
ssid-profile name tftc5
ssid T-yf5
max-sta-number 30
ssid-profile name Tguest
ssid T-G09
ssid-profile name default
vap-profile name tftc
service-vlan vlan-id 99
ssid-profile tftc
security-profile tftc
traffic-profile p1
vap-profile name T-yf5
service-vlan vlan-id 99
ssid-profile T-yf5
security-profile tftc
vap-profile name Tguest
service-vlan vlan-id 90
ssid-profile Tguest
security-profile Tguest
vap-profile name default
service-mode disable
wds-profile name default
mesh-handover-profile name default
mesh-profile name default
regulatory-domain-profile name default
regulatory-domain-profile name domain
air-scan-profile name default
rrm-profile name default
airtime-fair-schedule enable
dynamic-edca enable
sta-load-balance dynamic enable
sta-load-balance dynamic start-threshold 5
sta-load-balance dynamic gap-threshold 5
sta-load-balance dynamic deny-threshold 1
rrm-profile name rrmtftc
sta-load-balance dynamic enable
sta-load-balance dynamic start-threshold 5
sta-load-balance dynamic gap-threshold 5
sta-load-balance dynamic deny-threshold 1
radio-2g-profile name default
radio-2g-profile name ra2gtftc
rrm-profile rrmtftc
radio-5g-profile name default
radio-5g-profile name ra5gtftc
wids-profile name default
ap-system-profile name default
provision-ap
port-link-profile name default
wired-port-profile name default
ap auth-mode no-auth
ap-group name tftc
regulatory-domain-profile domain
radio 0
radio-2g-profile ra2gtftc
vap-profile tftc wlan 1
coverage distance 1
radio 1
vap-profile tftc wlan 1
ap-group name tftc5
radio 0
vap-profile default wlan 1
radio 1
vap-profile T-yf5 wlan 1
ap-group name Tguest
radio 0
vap-profile Tguest wlan 1
radio 1
vap-profile Tguest wlan 1
ap-group name default
ap-id 0 type-id 29 ap-mac 94** ap-sn 210**
ap-group tftc
radio 0
channel 20mhz 5
ap-id 1 type-id 29 ap-mac e8** ap-sn 210**
ap-group tftc
radio 0
channel 20mhz 3
ap-id 2 type-id 29 ap-mac 94** ap-sn 210**
ap-group Tguest
ap-id 3 type-id 29 ap-mac 94** ap-sn 210**
ap-group tftc
radio 0
channel 20mhz 8
ap-id 10 type-id 19 ap-mac 74** ap-sn 210**
ap-group tftc5
radio 0
radio disable
ap-id 11 type-id 19 ap-mac 74** ap-sn 210**
ap-group tftc5
radio 0
radio disable
ap-id 12 type-id 19 ap-mac 90** ap-sn 210**
ap-group tftc5
radio 0
radio disable
ap update sftp-server ip-address 192.168.0.199 sftp-username administrator sftp-password cipher %^%#4OSaR5