【实操】配置Telnet与SSH
发布作者:微思网络 发布时间:2025-05-26 浏览量:0次
实验目的
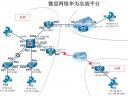
实验拓扑
实验需求
实验步骤
步骤1:设备的基本配置
配置R1:
Router>enable
Router#configure terminal
Router(config)#hostname R1
R1(config)#no ip domain-lookup
R1(config)#line console 0
R1(config-line)#exec-timeout 0 0
R1(config-line)#logging synchronous
R1(config-line)#exit
R1(config)#enable password xmws
R1(config)#interface ethernet0/0
R1(config-if)#ip address 192.168.1.254 255.255.255.0
R1(config-if)#no shutdown
R1(config-if)#exit
R1(config)#interface ethernet0/1
R1(config-if)#ip address 192.168.12.1 255.255.255.0
R1(config-if)#no shutdown
R1(config-if)#end
R1#
配置R2:
Router>enable
Router#configure terminal
Router(config)#hostname R2
R2(config)#no ip domain-lookup
R2(config)#line console 0
R2(config-line)#exec-timeout 0 0
R2(config-line)#logging synchronous
R2(config-line)#exit
R2(config)#enable password xmws
R2(config)#interface ethernet0/0
R2(config-if)#ip address 192.168.12.2 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#end
R2#
配置sw1:
Switch>enable
Switch#configure terminal
Switch(config)#hostname SW1
SW1(config)#no ip domain-lookup
SW1(config)#line console 0
SW1(config-line)#exec-timeout 0 0
SW1(config-line)#logging synchronous
SW1(config-line)#exit
SW1(config)#enable password xmws //必须设置,否则Telnet上SW1后无法进入特权模式
SW1(config)#interface vlan 1
SW1(config-if)#ip address 192.168.1.1 255.255.255.0
SW1(config-if)#no shutdown
SW1(config-if)#exit
SW1(config)#ip default-gateway 192.168.1.254
SW1(config)#end
SW1#
步骤2:配置Telnet
配置sw1:
SW1>enable
SW1#configure terminal
SW1(config)#line vty 0 4 //进入VTY
SW1(config-line)#password xmws //设置Telnet登录的密码为xmws
SW1(config-line)#login //启用密码
SW1(config-line)#transport input telnet //允许通过Telnet远程登录
SW1(config-line)#end
SW1#
步骤3:配置SSH 配置R2: 实验检查 步骤1:Telnet测试 步骤2:检查Telnet 步骤3:SSH测试 步骤4:检查SSH 华为认证R2>enable
R2#configure terminal
R2(config)#username xmws password wisdom //创建用户名和密码
R2(config)#ip ssh version 2 //启用SSH版本2
R2(config)#ip domain-name xmws.cn //定义域名
R2(config)#crypto key generate rsa //生成密钥
The name for the keys will be: R2.xmws.cn
Choose the size of the key modulus in the range of 360 to 4096 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
How many bits in the modulus [512]: 1024 //SSHv2密钥长度至少768位
% Generating 1024 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 0 seconds)R2(config)#
R2(config)#line vty 0 4
R2(config-line)#login local //使用用户名和密码验证
R2(config-line)# transport input ssh //允许通过SSH远程登录
R2(config-line)#end
R2#R1#telnet 192.168.1.1
Trying 192.168.1.1 ... Open
User Access Verification
Password:
SW1> //成功登录SW1
注意,如果SW1没有设置Enable密码,R1登录到SW1后输Enable会出现如下提示:
R1#telnet 192.168.1.1
Trying 192.168.1.1 ... Open
User Access Verification
Password:
SW1>enable
% No password set
同时按<Ctrl+Shit+6>组合键,然后再按x把界面切回R1
R1#show sessions //查看R1打开的Telnet会话
Conn Host Address Byte Idle Conn Name
* 1 192.168.1.1 192.168.1.1 6 5 192.168.1.1
R1#resume 1 //重新连接到SW1
[Resuming connection 1 to 192.168.1.1 ... ]
SW1>SW1#show users //SW1上查看谁登录到自己
Line User Host(s) Idle Location
* 0 con 0 idle 00:00:00
2 vty 0 idle 00:02:47 192.168.1.254
Interface User Mode Idle Peer Address
Location表示是谁登录到自己,192.168.1.254是R1。
SW1#clear line 2 //清除R1的Telnet连接
[confirm]
[OK]
SW1#show users
Line User Host(s) Idle Location
* 0 con 0 idle 00:00:00
Interface User Mode Idle Peer Address
R1已经被清除。R1#ssh -l xmws 192.168.12.2
Password:
R2>enable
Password:
R2# //成功登录到R2R2#show ssh
Connection Version Mode Encryption Hmac State Username
0 1.99 IN aes128-ctr hmac-sha2-256 Session started xmws
0 1.99 OUT aes128-ctr hmac-sha2-256 Session started xmws
2002年成立,专业认证培训20多年 面向全国招生→线上直播 | 线下面授 *网络技术:华为HCIA/ HCIP/HCIE;思科CCNA/CCNP/CCIE *Linux技术:红帽 RHCE/RHCA *K8S&容器:CKA/CKS *数据库:ORACLE OCP/ OCM ;MySQL ;达梦数据库 *虚拟化:VMware VCP/VCAP *安全认证:CISP体系/CISSP/ CISA;CCSK;CISAW体系 *管理类:PMP 项目管理;软考中/高项;ITIL体系;Togaf *其他课程如:DAMA;ACP;NPDP;Azure.信创认证....