【每日必学】怎么多站点site to site VPN
发布作者:微思网络 发布时间:2017-03-21 浏览量:0次
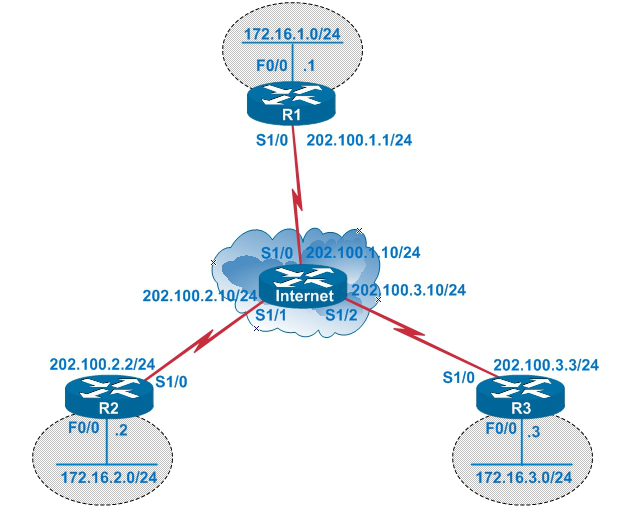
配置 Internet 路由器
interface Serial1/0
ip address 202.100.1.10 255.255.255.0 no shutdown
interface Serial1/1
ip address 202.100.2.10 255.255.255.0 no shutdown
interface Serial1/2
ip address 202.100.3.10 255.255.255.0 no shutdown
第一步:配置路由
配置 R1:
ip route 172.16.2.0 255.255.255.0 202.100.1.10 ip route 172.16.3.0 255.255.255.0 202.100.1.10 ip route 202.100.2.0 255.255.255.0 202.100.1.10 ip route 202.100.3.0 255.255.255.0 202.100.1.10
配置 R2:
ip route 172.16.1.0 255.255.255.0 202.100.2.10 ip route 172.16.3.0 255.255.255.0 202.100.2.10 ip route 202.100.1.0 255.255.255.0 202.100.2.10 ip route 202.100.3.0 255.255.255.0 202.100.2.10
配置 R3:
ip route 172.16.1.0 255.255.255.0 202.100.3.10 ip route 172.16.2.0 255.255.255.0 202.100.3.10 ip route 202.100.1.0 255.255.255.0 202.100.3.10 ip route 202.100.2.0 255.255.255.0 202.100.3.10
注:在实际应用中,企业都是通过配置默认路由到达 Internet,以上拓扑中可以在 R1,R2,R3 配置一条默认路由也可以解决路由问题,而且企业路由器也算是 Internet 边缘路由器,0.0.0.0 0.0.0 的路由到达 internet 必不可少:
分别在 R1,R2,R3 配置默认路由
R1: ip route 0.0.0.0 0.0.0.0 202.100.1.10
R2: ip route 0.0.0.0 0.0.0.0 202.100.2.10
R3: ip route 0.0.0.0 0.0.0.0 202.100.3.10
第二步:ISAKMP 策略配置 R1:
crypto isakmp policy 10 encr 3des
hash md5 authentication pre-share group 2
crypto isakmp key cisco address 202.100.2.2 crypto isakmp key cisco address 202.100.3.3
配置 R2:
crypto isakmp policy 10 encr 3des
hash md5 authentication pre-share group 2
crypto isakmp key 0 cisco address 202.100.1.1 crypto isakmp key 0 cisco address 202.100.3.3
配置 R3:
crypto isakmp policy 10 encr 3des
hash md5 authentication pre-share group 2
crypto isakmp key cisco address 202.100.1.1 crypto isakmp key cisco address 202.100.2.2
第三步:ISAKMP 策略配置 IPSEC 转换集
配置 R1: crypto ipsec transform-set myset esp-3des esp-sha-hmac
配置 R2: crypto ipsec transform-set myset esp-3des esp-sha-hmac
配置 R3: crypto ipsec transform-set myset esp-3des esp-sha-hmac
第四步:感兴趣流量配置 R1:
Access-list 100 permit ip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255
Access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
配置 R2:
Access-list 100 permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
Access-list 101 permit ip 172.16.2.0 0.0.0.255 172.16.3.0 0.0.0.255
配置 R3:
Access-list 100 permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255
Access-list 101 permit ip 172.16.3.0 0.0.0.255 172.16.2.0 0.0.0.255
第五步:配置 crypto map
配置 R1:
crypto map mymap 10 ipsec-isakmp set peer 202.100.2.2
match address 100
set transform-set myset
crypto map mymap 20 ipsec-isakmp set peer 202.100.3.3
match address 101
set transform-set myset
配置 R2:
crypto map mymap 10 ipsec-isakmp set peer 202.100.1.1
match address 100
set transform-set myset
crypto map mymap 20 ipsec-isakmp set peer 202.100.3.3
match address 101
set transform-set myset
配置 R3:
crypto map mymap 10 ipsec-isakmp set peer 202.100.1.1
match address 100
set transform-set myset
crypto map mymap 20 ipsec-isakmp set peer 202.100.2.2
match address 101
set transform-set myset
第六步:在相应的接口应用 crypto map
配置 R1:
int s1/0
crypto map mymap
配置 R2:
int s1/0
crypto map mymap
配置 R3:
int s1/0
crypto map mymap
第六步:测试
R1#ping 172.16.2.2 source 172.16.1.1
R1#ping 172.16.3.3 source 172.16.1.1
或
R2#ping 172.16.1.1 source 172.16.2.2
R2#ping 172.16.3.3 source 172.16.2.2
或
R3#ping 172.16.1.1 source 172.16.3.3
R3#ping 172.16.2.2 source 172.16.3.3
常用检查命令:
show crypto isakmp policy show crypto ipsec transform-set show crypto isakmp sa
show crypto ipsec sa show crypto map
clear cryto sa
clear crypto sa peer (ip address|peer name) clear crypto sa map (map name)
Debug cryto isakmp
Debug cryto ipsec